Encryption (Encryptor)
PREMIUM FEATURE¶
The zero-knowledge encryption capability lets you create an encrypted folder on any storage linked to your odrive. You choose your own passphrase. Your passphrase is never seen or stored on any server. You can turn vanilla storage into strongly encrypted, secure cloud storage.
️ IMPORTANT
Only you will know the passphrase, so do not lose it! Without your passphrase you cannot access your files. We have no way of helping you to recover your passphrase if you forget it.
HOW TO SETUP ODRIVE ENCRYPTED FOLDERS¶
Follow the instructions below to get started. You may also find this short video to be helpful.
-
Open up a web browser and navigate to the odrive Encryptor section https://www.odrive.com/account/myodrive?catid=encryption
-
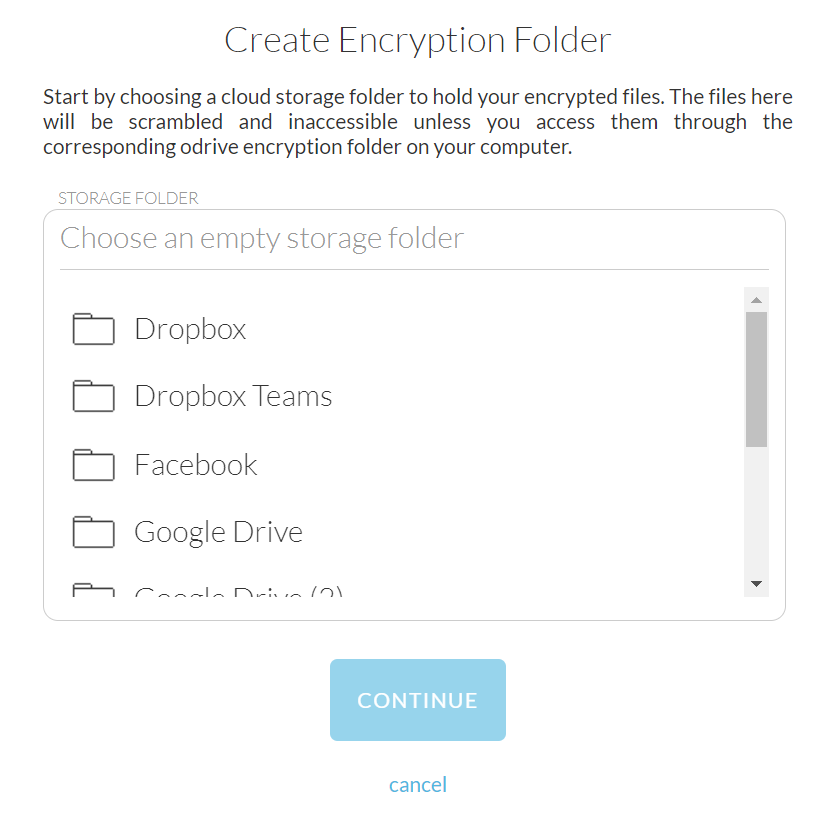
Click "Create encryption folder" to open the setup form. You'll see a folder selection dialog that initially shows the all of your linked storage folders that you are used to seeing at the root of your odrive folder.
-
Choose a storage source and then navigate to an empty folder you want to use as the remote storage location. You can use the create folder button if you want to make a new subfolder. The location should be empty. Encryptor will ignore any existing files in the chosen folder.
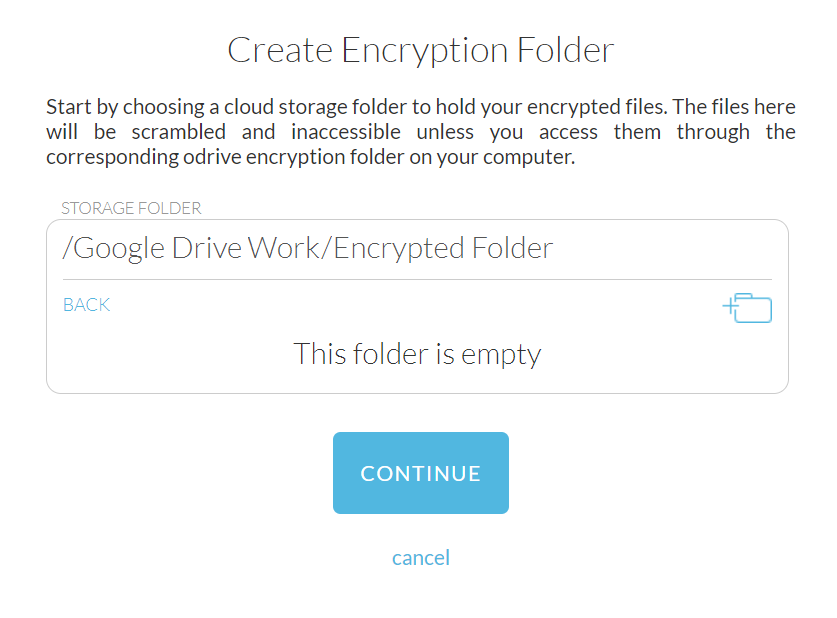
Choosing a remote storage location
Since encrypted data will appear as long, alphanumeric folder/file names on the remote storage, we recommend you create Encryptor folders within a subfolder, as opposed to directly in the root folder. This will prevent confusion when viewing these locations outside of odrive.
- Now, you will be asked to pick an encryption name. This is what the encrypted folder will be named on the local side; on your computer, you'll go to your odrive folder under /Encryptor/your-chosen-encryption-name/ to access your files.
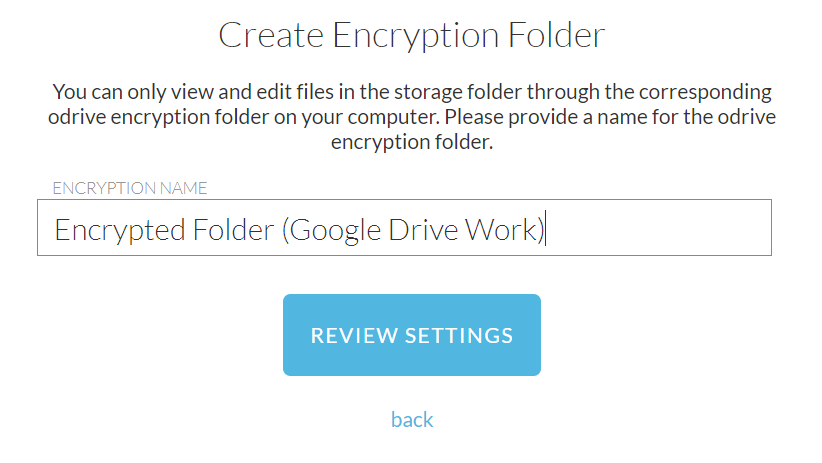
Choosing a local encryption folder name
To access the folder locally on your computer, odrive will present the encryption folder inside of a new "Encryptor" folder at the root of your odrive folder. Because of this, you may want to include something about the remote storage provider used for the Encryptor folder so that you can easily remember what storage is backing each Encryptor folder.
Examples: Encrypted Folder (Google Drive Work) Sensitive Documents (Amazon S3)
-
After choosing a local encryption name, you'll be given a chance to review the final settings before you create the new encrypted folder. Be sure to verify that the remote storage location and the local encryption folder name represent the encryption folder relationship that you had in mind.
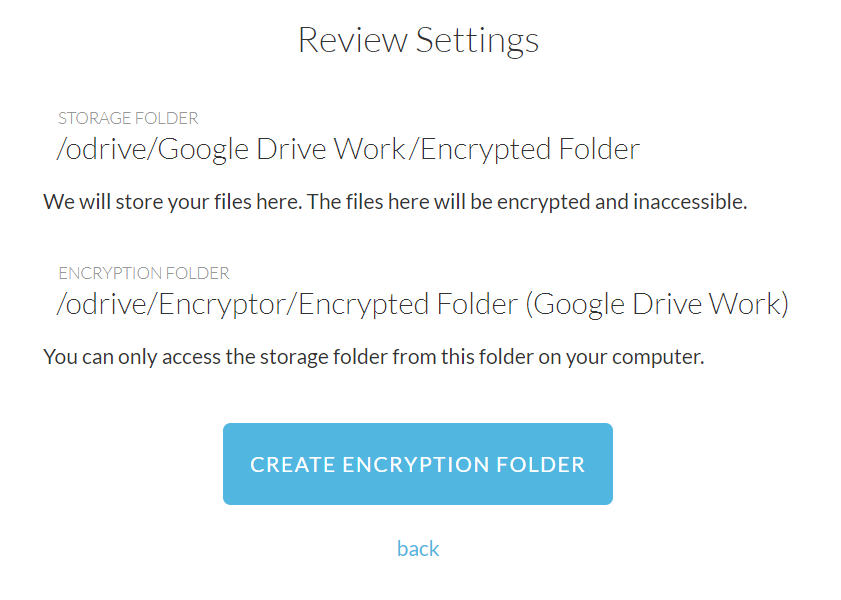
-
If you are satisfied that the settings are correct, you can finish the encryption folder creation process.
ACCESSING YOUR ENCRYPTOR FOLDERS¶
Once you have created a new Encryptor folder, that folder will show up inside the "Encryptor" folder within the odrive folder on your desktop
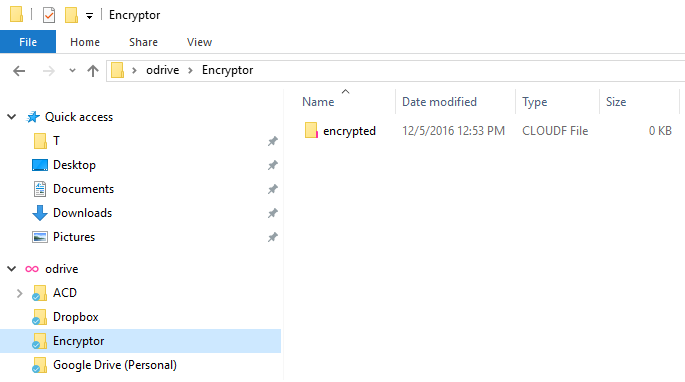
You can set up as many encrypted folders as you need, and each encryption folder can use a different secret passphrase.
Automatic sync must be turned on for encryption folders to work
Make sure that odrive automatic synchronization has not been stopped. Automatic synchronization needs to be enabled to ensure that the Encryptor folders are reflected in the odrive desktop application (and to ensure that any changes made to files or new files added within Encryptor will be properly scrambled and uploaded to remote storage).
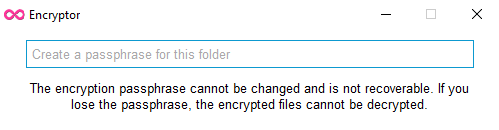
Setting your secret passphrase¶
The first time you access the Encryptor folder on your computer, odrive will ask you for the secret passphrase. If a passphrase has not been setup before, this is where you will specify what you want the passphrase to be (dialogue appears in the background).
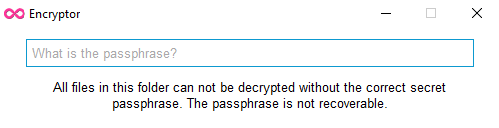
If a passphrase has previously been set, then you will need to enter that to decrypt your files.
HOW OUR ENCRYPTION WORKS¶
Data Encryption:
- Generate a random 64-bit salt (S)
- Generate a 128-bit key (K) using PBKDF2 with S and the user’s passphrase (P), 5000 iterations, and HMAC-SHA256 for PRF
- Generate a random 128-bit initialization vector (IV)
- Compute a hash (H) of the file data using SHA256
- Plaintext (PT) is: (file data + H + PKCS #7 padding to the next multiple of 16 bytes)
- Generate the ciphertext (CT) using AES-CBC to encrypt PT using the K and IV
- Get the 8-bit internal odrive Encryption version designation (V)
- Write to output file V+S+IV+CT
Data Decryption:
- Read V, S, and IV from the beginning of the encrypted file
- Derive K using S and P
- Decrypt the CT using K and IV to plaintext (PT)
- Unpad the PT
- Strip H from the end of PT
- Calculate new hash (H2) of the resulting PT and compare to H
File/Folder Name Encryption:
- Generate a random 64-bit salt (S)
- Generate a 128-bit key ( K ) using PBKDF2 with S and the user’s passphrase (P), 5000 iterations, and HMAC-SHA256 for PRF
- Generate a random 128-bit initialization vector (IV)
- Plaintext (PT) is: (4 zero bytes + the filename + PKCS #7 padding to the next multiple of 16 bytes)
- Get the ciphertext (CT) using AES-CBC to encrypt the PT using the K and IV
- Get the 8-bit internal odrive Encryption version designation (V)
- URL-safe, base64 encode (V+S+IV+CT)
Can I turn off encrypting file and folder names but still have the file content encrypted?
Yes, there is a disableEncryptedNames advanced client setting which can be used to turn off scrambling file and folder names.
File/Folder Name Decryption:
- Decode URL-safe, base64 filename
- Read V, S, and IV from the beginning of the decoded filename
- Derive K using S and P
- Decrypt the CT using K and IV
- Check that the new filename starts with 4 zero bytes
- Strip zero bytes and padding
Where is the Key Stored? The key itself is never stored.
The key is derived from the salt and your passphrase, as described above. The passphrase is stored on the local system (and only the local system), once you enter it for the first time. It is stored to prevent needing to continually enter the passphrase. There is an advanced feature to turn this off, so that you have to enter the passphrase every time you restart odrive.
The passphrase is kept in the keychain on MacOS and in an encrypted registry entry on Windows using Microsoft’s CryptoAPI.
Does Encryption affect file size? Files sizes increase due to the additional information prepended to the ciphertext and the hash that is appended to the plaintext. The plaintext also needs to be padded to a multiple of the block size. The amount of padding needed will vary, depending on the size of the original file.
What happens to my encrypted data if I choose to cancel my Premium subscription? You will still be able to access all of your Encrypted data. Encryptor folders switch to read-only mode.
ADDITIONAL RESOURCES¶
A command line python utility was created by one of our Engineers to allow decryption of Encryptor content outside of odrive. https://github.com/amagliul/odrive-utilities